As an ethical hacker, you will need to understand various hacking techniques such as −
As a final note, it is highly recommended that you refrain from engaging yourself in black hat hacking which may spoil your entire career.
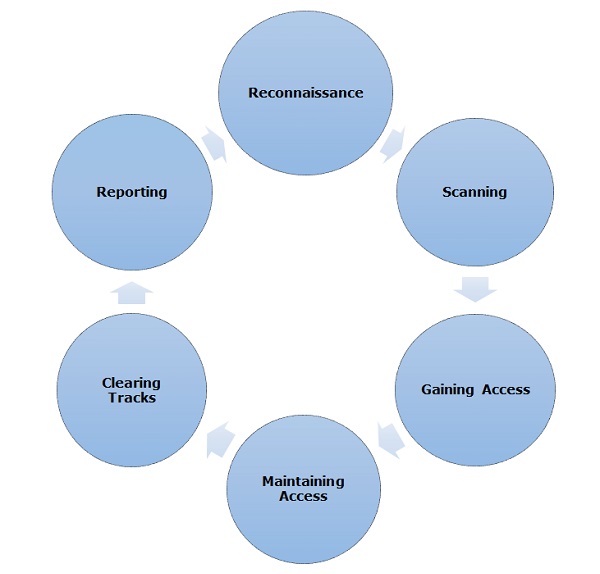
Different security training manuals explain the process of ethical hacking in different ways, but for me as a Certified Ethical Hacker, the entire process can be categorized into the following six phases.
- Password guessing and cracking
- Session hijacking
- Session spoofing
- Network traffic sniffing
- Denial of Service attacks
- Exploiting buffer overflow vulnerabilities
- SQL injection
Basic Skills
Computer Hacking is a Science as well as an Art. Like any other expertise, you need to put a lot of effort in order to acquire knowledge and become an expert hacker. Once you are on the track, you would need more effort to keep up-to-date with latest technologies, new vulnerabilities and exploitation techniques.- An ethical hacker must be a computer systems expert and needs to have very strong programming and computer networking skills.
- An ethical hacker needs to have a lot of patience, persistence, and perseverance to try again and again and wait for the required result.
Courses & Certifications
This tutorial provides the basic guidelines to become a successful Ethical Hacker. If you want to excel in this field, then you might choose to pursue the following courses and certifications −- Obtain a bachelor’s degree in Computer Science or A+ Certificate to gain an understanding of the most common hardware and software technologies.
- Get into a programmer’s role for a few years and then switch to get a tech support position.
- Proceed to get network certifications like Network+ or CCNA and then security certifications like Security+, CISSP, or TICSA.
- It is recommended that you get some work experience as a Network Engineer and System Administrator to understand networks and systems inside out.
- Keep going through various books, tutorials and papers to understand various computer security aspects and take them as a challenge to secure your network and computer systems as network security engineer.
- Study courses which cover creating Trojan horses, backdoors, viruses, and worms, denial of service (DoS) attacks, SQL injection, buffer overflow, session hijacking, and system hacking.
- Master the art of penetration testing, footprinting and reconnaissance, and social engineering.
- Finally go for a Certified Ethical Hacker (CEH) Certification.
Final Note
You need to stay as a White Hat Hacker which means you need to work within given boundaries. Never intrude or attack any computer or network without a required permission from the authorities.As a final note, it is highly recommended that you refrain from engaging yourself in black hat hacking which may spoil your entire career.
Ethical Hacking - Process
Like all good projects, ethical hacking too has a set of distinct phases. It helps hackers to make a structured ethical hacking attack.Different security training manuals explain the process of ethical hacking in different ways, but for me as a Certified Ethical Hacker, the entire process can be categorized into the following six phases.

Comments
Post a Comment