Exploitation is a piece of programmed software or script which can
allow hackers to take control over a system, exploiting its
vulnerabilities. Hackers normally use vulnerability scanners like
Nessus, Nexpose, OpenVAS, etc. to find these vulnerabilities.
Metasploit is a powerful tool to locate vulnerabilities in a system.
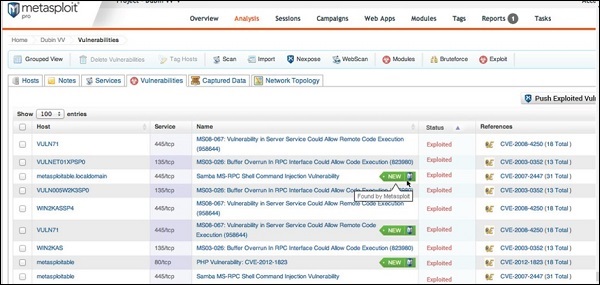 Based on the vulnerabilities, we find exploits. Here, we will discuss
some of the best vulnerability search engines that you can use.
Based on the vulnerabilities, we find exploits. Here, we will discuss
some of the best vulnerability search engines that you can use.
NVD includes databases of security checklists, security-related software flaws, misconfigurations, product names, and impact metrics.
 In general, you will see that there are two types of exploits −
In general, you will see that there are two types of exploits −
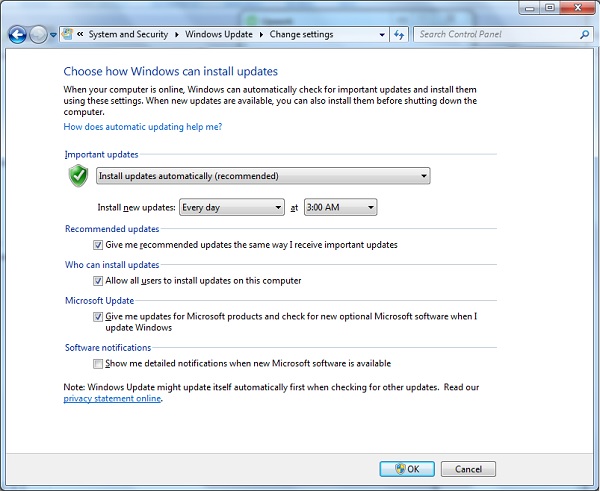
In Windows environment, you can activate automatic updates by using the options available in the Control Panel → System and Security → Windows Updates.
 In Linux Centos, you can use the following command to install automatic update package.
In Linux Centos, you can use the following command to install automatic update package.
Metasploit is a powerful tool to locate vulnerabilities in a system.
 Based on the vulnerabilities, we find exploits. Here, we will discuss
some of the best vulnerability search engines that you can use.
Based on the vulnerabilities, we find exploits. Here, we will discuss
some of the best vulnerability search engines that you can use.Exploit Database
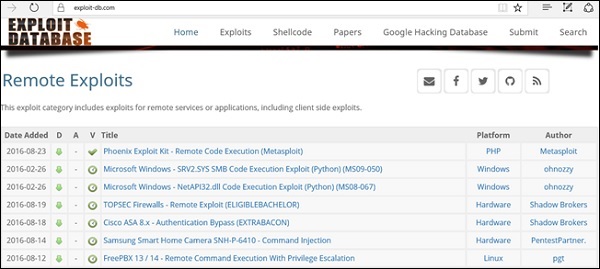
www.exploit-db.com is the place where you can find all the exploits related to a vulnerability.
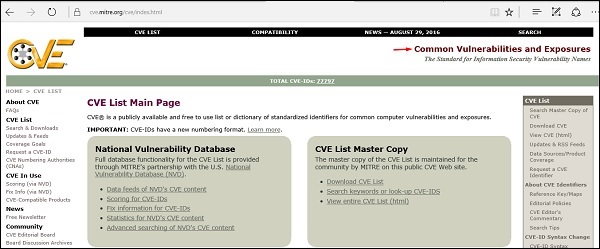
Common Vulnerabilities and Exposures
Common Vulnerabilities and Exposures (CVE) is the standard for information security vulnerability names. CVE is a dictionary of publicly known information security vulnerabilities and exposures. It’s free for public use. https://cve.mitre.org
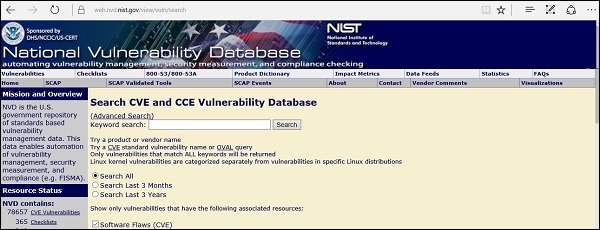
National Vulnerability Database
National Vulnerability Database (NVD) is the U.S. government repository of standards based vulnerability management data. This data enables automation of vulnerability management, security measurement, and compliance. You can locate this database at − https://nvd.nist.govNVD includes databases of security checklists, security-related software flaws, misconfigurations, product names, and impact metrics.
 In general, you will see that there are two types of exploits −
In general, you will see that there are two types of exploits −- Remote Exploits − These are the type of exploits where you don’t have access to a remote system or network. Hackers use remote exploits to gain access to systems that are located at remote places.
- Local Exploits − Local exploits are generally used by a system user having access to a local system, but who wants to overpass his rights.
Quick Fix
Vulnerabilities generally arise due to missing updates, so it is recommended that you update your system on a regular basis, for example, once a week.In Windows environment, you can activate automatic updates by using the options available in the Control Panel → System and Security → Windows Updates.
 In Linux Centos, you can use the following command to install automatic update package.
In Linux Centos, you can use the following command to install automatic update package.
Comments
Post a Comment