Like all good projects, ethical hacking too has a set of distinct
phases. It helps hackers to make a structured ethical hacking attack.
Different security training manuals explain the process of ethical
hacking in different ways, but for me as a Certified Ethical Hacker, the
entire process can be categorized into the following six phases.
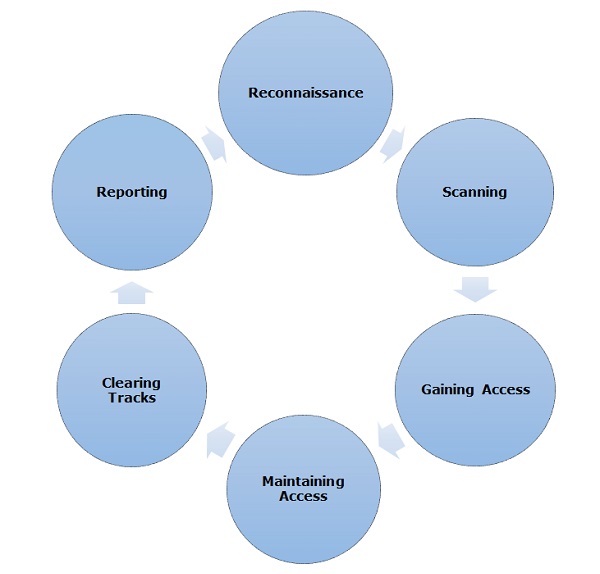
Reconnaissance
Reconnaissance is the phase where the attacker gathers information
about a target using active or passive means. The tools that are widely
used in this process are NMAP, Hping, Maltego, and Google Dorks.
Scanning
In this process, the attacker begins to actively probe a target
machine or network for vulnerabilities that can be exploited. The tools
used in this process are Nessus, Nexpose, and NMAP.
Gaining Access
In this process, the vulnerability is located and you attempt to
exploit it in order to enter into the system. The primary tool that is
used in this process is Metasploit.
Maintaining Access
It is the process where the hacker has already gained access into a
system. After gaining access, the hacker installs some backdoors in
order to enter into the system when he needs access in this owned system
in future. Metasploit is the preferred tool in this process.
Clearing Tracks
This process is actually an unethical activity. It has to do with the
deletion of logs of all the activities that take place during the
hacking process.
Reporting
Reporting is the last step of finishing the ethical hacking process.
Here the Ethical Hacker compiles a report with his findings and the job
that was done such as the tools used, the success rate, vulnerabilities
found, and the exploit processes.
Quick Tip
The processes are not standard. You can adopt a set of different
processes and tools according to your techniques that you are
comfortable with. The process is of least significance as long as you
are able to get the desired results.


Comments
Post a Comment